選択した画像 opsec process parts 349137-Opsec process parts
OPSEC is an analytical process to identify Critical Information (CI), identify threats to that Critical Information and the related vulnerabilities and risks of exploitation to that CI, and identify, develop, and implement countermeasures to protect that CIMay 19, · OPSEC's most important characteristic is that it is a process OPSEC is not a collection of specific rules and instructions that can be applied to every operation It is a methodology that can be applied to any operation or activity for the purpose of denying critical information to an adversaryOperations Security (OPSEC) Plan For Subcontract No * Name* Date * Ensure Proper Classification of Document When Complete INTRODUCTION OPSEC is a systematic and proven process by which CONTRACTOR and its supporting subcontractors can deny to potential adversaries information about capabilities and intentions by identifying, controlling and

Ppt Operations Security Opsec Powerpoint Presentation Free Download Id
Opsec process parts
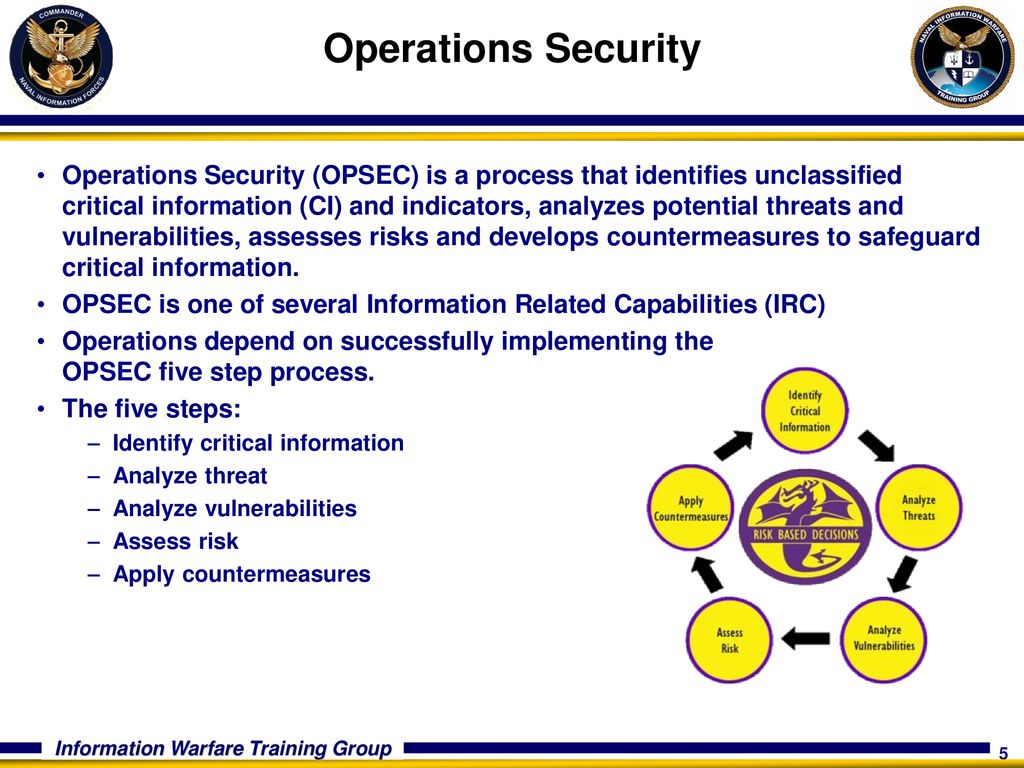
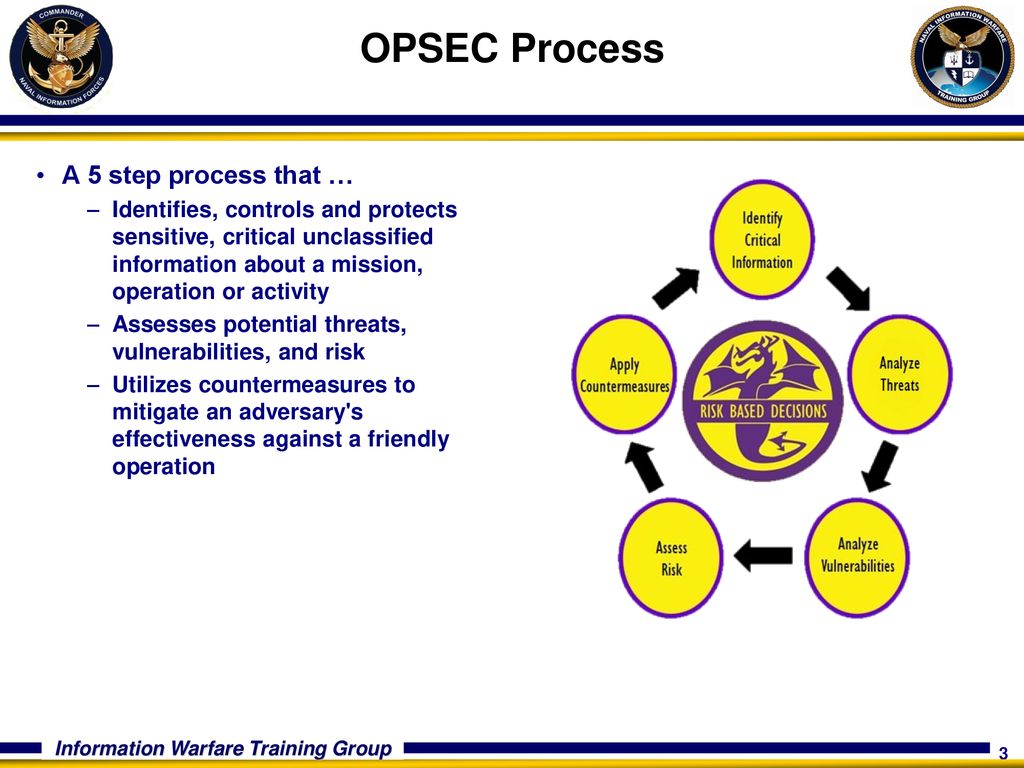
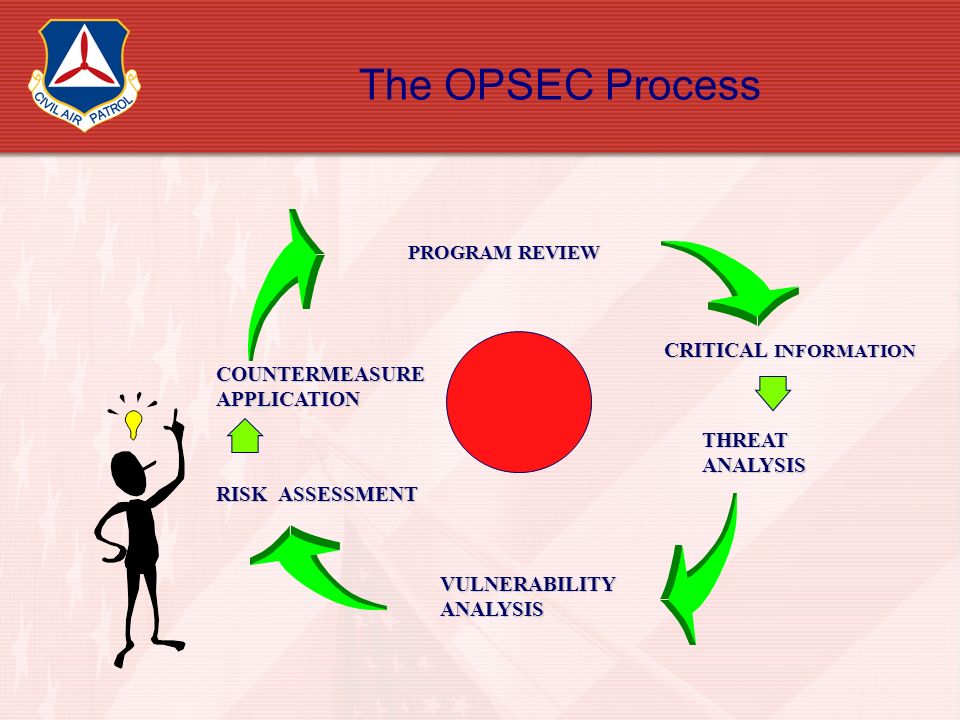
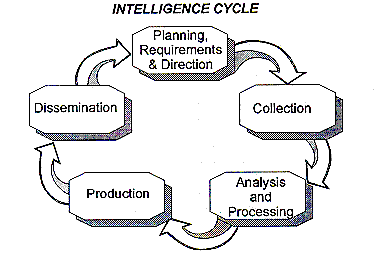
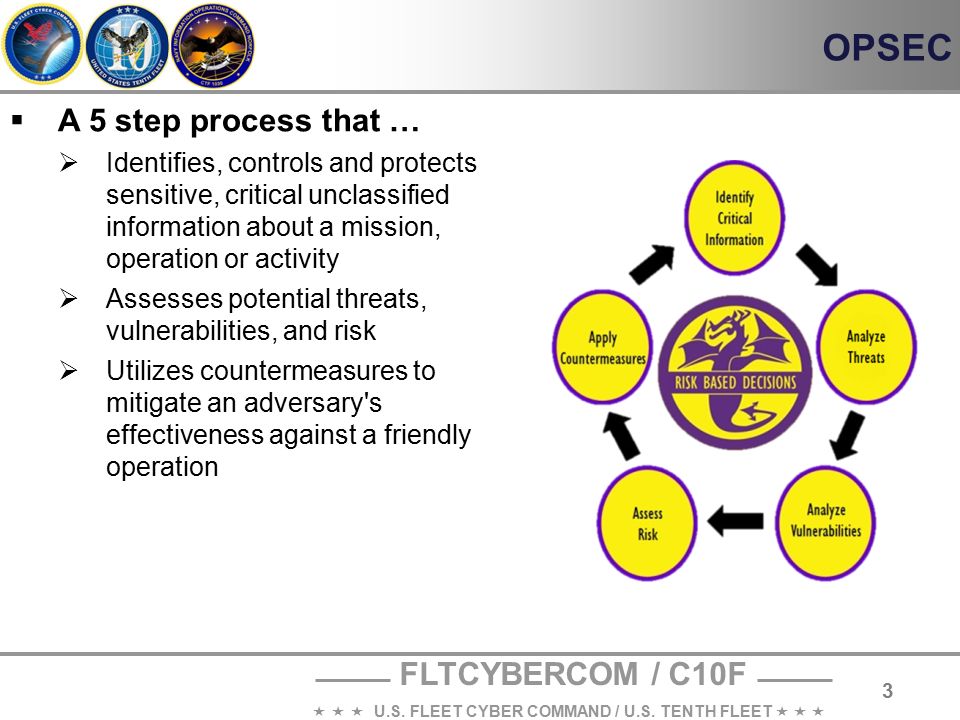
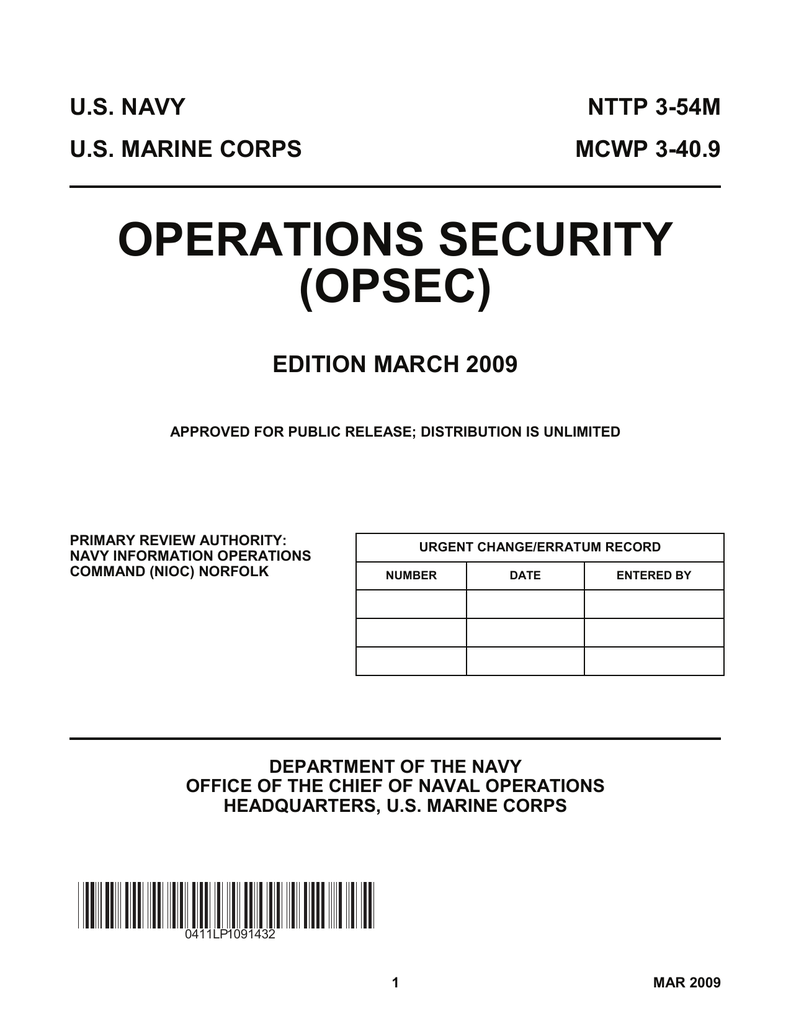
Opsec process parts-Operations Security (OPSEC) is a process that identifies unclassified critical information (Cl) and indicators, analyzes potential threats and vulnerabilities, assesses risks and develops countermeasures to safeguard critical information OPSEC is one Of several Information Related Capabilities (IRC)Operations Security (OPSEC) Operations Security is the systematic and proven process by which potential adversaries can be denied information about capabilities and intentions by identifying, controlling and protecting generally unclassified evidence of the planning and execution of sensitive activities The process involves five steps




Operations Security Opsec Program Pdf Free Download
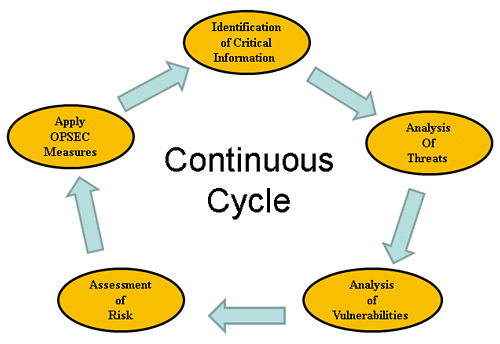
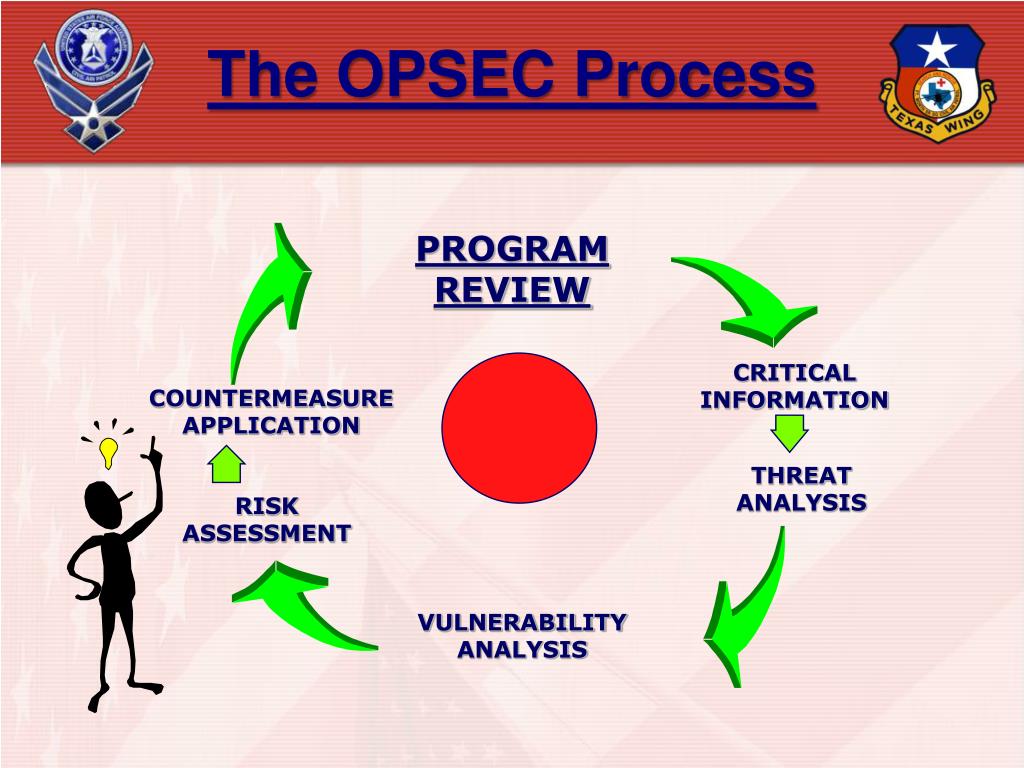
Aug 05, · Operations security (OPSEC) is a process that identifies friendly actions that could be useful for a potential attacker if properly analyzed and grouped with other data to reveal critical information or sensitive dataOPSEC uses countermeasures to reduce orSelect all that apply Got this wrong OPSEC Process Five Steps Identification Analysis of threats Analysis of vulnerabilities Assessment of risks Application of appropriate countermeasures Which of the following must be reported?The OPSEC process identifies critical information and determines when that information may cease to be critical in the life cycle of an operation, program, or activity Analysis of Threats Threat analysis consists of determining the adversary's ability to collect, process, analyze, and use information The objective of threat analysis is to
Operations Security (OPSEC) is the process by which we protect critical information whether it is classified or unclassified that can be used against us It focuses on preventing our adversaries' access to information and actions that may compromise an operationThe OPSEC process includes the following five steps (1) identify critical information, (2) identify the threat, (3) assess vulnerabilities, (4) analyze the risk, (5) develop and apply countermeasures Operations Security Countermeasures Methods and meansMay 08, 21 · OPSEC's most important characteristic is that it is a process OPSEC is not a collection of specific rules and instructions that can be applied to every operation It is a methodology that can be applied to any operation or activity for the purpose of denying critical information to an adversary
Feb 29, · What are parts of the opsec process?Industrial Counterfeit industrial parts result in staggering repair and warranty costs in addition to the threat to public safety From bolts to ball bearings, switches to springs, plugs to pressure valves, OpSec increases the integrity of your products and your brand 500 Commercial airplanes possibly affected by falsified airplane parts inDerivative classifiers are required to have all the following except ______ a security clearance derivative classification training a needtoknow approval of the original classification authority (OCA) approval of the original classification authority (OCA) Which of the following are parts of the OPSEC process?




Pdf Opsec Model And Applications M Kubilay Akman Academia Edu



Www Ceeol Com Content Files Document 7396 Pdf
Jan 10, 08 · OPSEC indicators are friendly detectable actions and opensource information that can be collected, interpreted or pieced together by an adversary to derive Critical Information More simply, Critical Information is the pieces of the puzzle that add up to complete the pictureEach correct answer represents a part of the solution Choose all that apply A Analysis of Vulnerabilities B Display of associated vulnerability components C Assessment of Risk D Identification of Critical InformationSep 29, 14 · Which of the following are the process steps of OPSEC?




Threat Model Att Ck Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks



Opsec General Military Training Dd Mmm Yy Ppt Download
Analysis of threats, application of appropriate countermeasures, conduct vulnerability assessments Which of the following materials are subject to prepublication review?OPSEC isn't just a set of rules that tells you what you should or shouldn't say • It's a process;This webbased course provides OPSEC awareness for military members, government employees, and contractors The course provides information on the basic need to protect unclassified information about operations and personal information to ensure safe and successful operations and personal safety



Command Indoctrination Operations Security Dd Mmm Yy Ppt Download




Operations Security Opsec U S Navy
Define OPSEC a OPSEC is a process of analyzing friendly actions pursuant to military operations and other activities to(1) Identify those friendly actions that can be observed by the threat (2) Determine indicators that the threat might obtain that could be interpreted or pieced together toSep 28, 11 · Then you have used OPSEC!Aug 24, · Identify critical information, identify the threat, assess vulnerabilities, analyze the risk, develop and apply countermeasures, are parts of the OPSEC process




Operations Security Wikipedia



Www Marines Mil Portals 1 Mco 3070 2a Pdf
A method of denying critical information to an adversary • A fivestep process to identify, control and protect critical information and analyzeJul 06, 16 · The OPSEC process has five steps which are as follows 1Identification of Critical Information Identifying information vitally needed by an adversary, which focuses the remainder of the OPSEC process on protecting vital information, rather than attempting to protect all classified or sensitive unclassified information 2Analysis of ThreatsOpSec developed a security label that consolidated variable GM parts data with anticounterfeiting technology and serialization for itemized tracking The novel solution design met the threefold requirements in a single label construction As a result, the label was easy to integrate into the supply chain process



Security Awareness Training Ppt Video Online Download




Ttp Opsec Acronym
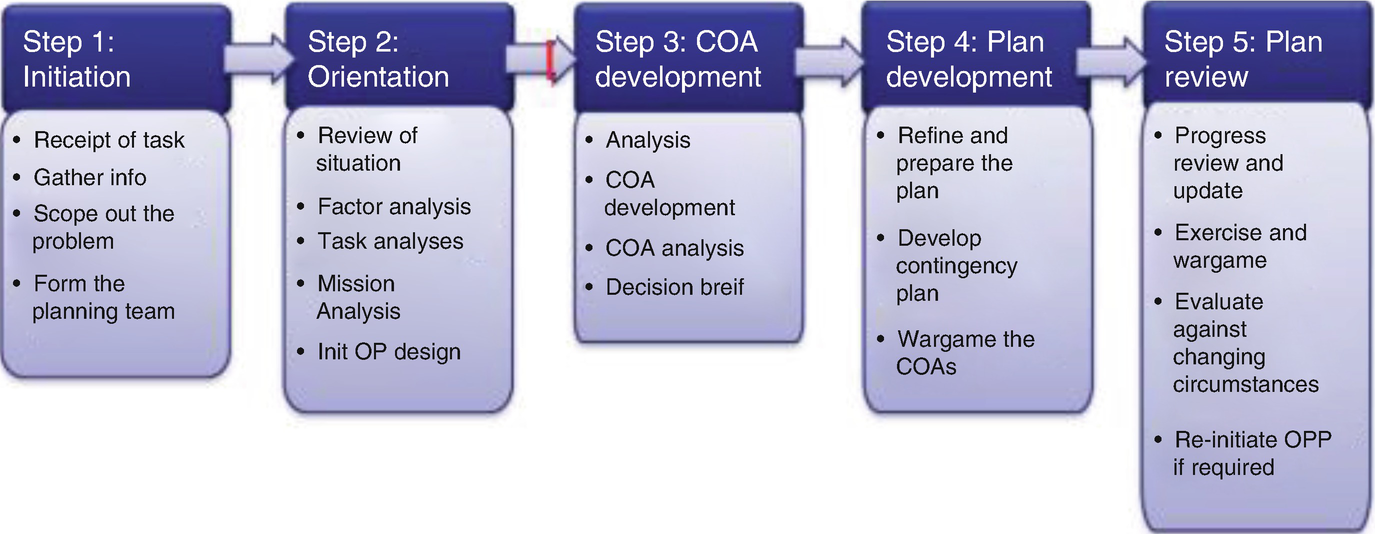
The OPSEC process is applicable across the range of mi litary operations Use of the process ensures that the resulting OPSEC counter measures address all significant aspects of the particular situation and are balanced against operational requirements OPSEC is a continuous process The OPSEC process (Figure II1) consists of five distinctJul 24, 12 · The OPSEC process consists of Five Steps which can apply to any plan, operation, program, project or activity Thesesteps provide a framework for the systematic processAT & OPSEC in the Contract Support Process This table provides a detailed sequential stepbystep process, including the staff officer lead for each step • Part III ATO/OPSEC Risk Analysis and Assessment Checklist The ATO is the focal point for all staff planning required to properly integrate necessary ATrelated



What Is Opsec Operations Security




Operations Security Opsec And Cyber Security Training For Aerojet Rocketdyne Suppliers January 28 19 Presenter Scmm Compliance Ppt Download
About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How works Test new features Press Copyright Contact us Creators(2) OPSEC Awareness Education and Training will be provided or coordinated through government channels (NUWCDIVKPT OPSEC Program, IOSS, etc) as a expense within the Cost Management Process when developing a project bid All personnel supporting the contract will receive initial OPSEC awareness training and annual OPSEC Refresher trainingJul 24, · Identify critical information, identify the threat, assess vulnerabilities, analyze the risk, develop and apply countermeasures, are parts of the OPSEC process Log in for more information This answer has been confirmed as correct and helpful




Touxwb6yzsjam




Opsec For Android Apk Download
The OPSEC Process Identify Critical Information Information about friendly (US, allied, and/or coalition) activities, intentions, capabilities, or limitations an adversary seeks in order to gain a military, political, diplomatic, economic, or technological advantageAll of the above 21Which of the following are parts of the OPSEC process?




Mco 3070 2 The Marine Corps Operations Security Opsec Program




The Five Military Opsec Steps That Businesses Can Learn From Techrepublic
OpSec developed a security label that consolidated variable GM parts data with anticounterfeiting technology and serialization for itemized tracking The novel solution design met the threefold requirements in a single label construction As a result, the label was easy to integrate into the supply chain processSep 01, 11 · Operational Security (OPSEC) which is the evaluation and control of any critical information that could be used against you by an adversary The result of good OPSEC is the elimination or withholding of the most damaging information that your adversary has the ability to gather and understand how to use against you OPSEC happens everyday When you go onJul 24, · Jozeal Identify critical information, identify the threat, assess vulnerabilities, analyze the risk, develop and apply countermeasures, are parts of the OPSEC process Log in for more information Added 339 days ago7/24/ PM This answer has been confirmed as correct and helpful




What Is Operational Security The Five Step Process Best Practices And More Digital Guardian



Www Mcieast Marines Mil Portals 33 Mcieast Mcb camlejo 3070 1 Pdf Ver 19 02 12 000
The OPSEC process is an integral part of force protection, helping protect service members, civilian employees, family members, facilities, and equipment at all locations and in all situations Antiterrorism relies heavily on OPSEC as a means of denying terrorists targeting information Since force protection and antiterrorOPSEC is a process of identifying, analyzing and controlling critical information indicating friendly actions associated with military operations and other activities True or False Any step in the OPSEC process may need to be revisited at any timeOPSEC Process Five Steps STUDY Flashcards Learn Write Spell Test PLAY Match Gravity Created by Katie_Cassidy30 Terms in this set (29) Identification of critical information The information that an adversary would need in order to degrade services, disrupt operations, and impact the reputation of an organization



Info Publicintelligence Net Ioss Terrorismthreathandbook Pdf



Www Standards Doe Gov Standards Documents 10 1233 Bhdbk 19 Images File
Start studying Fivestep of OPSEC process Learn vocabulary, terms, and more with flashcards, games, and other study tools Scheduled maintenance Saturday, June 5 from 4PM to 5PM PDT* Security is Everyone's Responsibility – See Something, Say Something!Jun 06, 03 · The OPSEC process is an integral process of force protection to help protect Service members, civilian employees, family members, facilities, and equipment at all locations and in all situations Force protection relies heavily on OPSEC as a means of denying targeted



Www Standards Doe Gov Standards Documents 10 1233 Bhdbk 19 Images File



Opsec Latest Version For Android Download Apk
Operations security (OPSEC) is a process that identifies critical information to determine if friendly actions can be observed by enemy intelligence, determines if information obtained by adversaries could be interpreted to be useful to them, and then executes selected measures that eliminate or reduce adversary exploitation of friendly critical informationOperations Security (OPSEC) Process Analytical process that involves five components identification of critical information, analysis of threats, analysis of vulnerabilities, assessment of risks, and application of appropriate countermeasuresMar 24, 17 · OPSEC is an analytical process used to deny an adversary information (generally unclassified) concerning our intentions and capabilities by identifying, controlling, and protecting indicators associated with our planning processes or operations



Section 2 Intelligence Collection Activities And Disciplines Operations Security Intelligence Threat Handbook




Operations Security Opsec Program Pdf Free Download
The OPSEC FiveStep Process is a process meant to prevent the inadvertent release of Critical Information If individuals protect their pieces of the puzzle, adversaries will not be successful in obtaining a piece that could be aggregated with other information resulting in adverse consequences to our missionAug 12, · Operations Security (OPSEC) is a capability that uses a process to preserve friendly essential secrecy by identifying, controlling and protecting critical information and indicators that would allow adversaries or potential adversaries to identify and exploit friendly vulnerabilitiesOPSEC is a risk management instrument that enables a manager or commander to view an operation or activity from the perspective of an adversary It is a process of identifying, analyzing and controlling critical information



Cyber Operational Planning Springerlink




Opsec History And Basics
Mar 15, 21 · 19 Which of the following are parts of the OPSEC process?Operations Security (OPSEC) Plan For Subcontract No * Name* Date * Ensure Proper Classification of Document When Complete INTRODUCTION OPSEC is a systematic and proved process by which CONTRACTOR and its supporting subcontractors can deny to potential adversaries information about capabilities and intentions by identifying, controlling and




Operations Security Opsec Program Pdf Free Download




Automotive Opsec




Operations Security Wikipedia




Operations Security Opsec Program Pdf Free Download



Media Defense Gov Oct 28 1 1 0 Nttp 3 13 3m Mctp 3 32b Opsec 17 Pdf




The Art And Practice Of Opsec By T H Survivalblog Com




The Opsec Process The Opsec Process Tasks Security Contemplations Must Be Fundamental To The Way Toward Getting Ready For Arranged And Touchy Course Hero




David Groep Nikhef Pdp Trust Policy Coordination Opsec



Www Mcieast Marines Mil Portals 33 Mcieast Mcb camlejo 3070 1 Pdf Ver 19 02 12 000



Overall Classification Of This Briefing Is Unclassified Fouo Ppt Video Online Download



Static E Publishing Af Mil Production 1 Af A3 Publication Afi10 701 Afi10 701 Pdf



Chips Articles New Navy Opsec App Is Out




Why Cyber Security Is Necessary And Best For 21 Iknowa2z I Know A Z




Operations Security Opsec Good Security Is A Group Effort Ppt Video Online Download




Opsec Flashcards Quizlet




Opsec Operations Security Opsec Annual Refresher Course I Introduction Ii Critical Information A Process Made Of 5 Steps 1 Identification Of Critical Course Hero




Opsec For Pc Free Download Windows 7 8 10 Edition



Www Esd Whs Mil Portals 54 Documents Dd Issuances Dodm 5502m Pdf




Energy System Resilience



Www Mcieast Marines Mil Portals 33 Mcieast Mcb camlejo 3070 1 Pdf Ver 19 02 12 000



Usacac Army Mil Sites Default Files Documents Fmpc Atp 3 13 3 Army Operations Security For Division And Below Pdf



Media Defense Gov Oct 28 1 1 0 Nttp 3 13 3m Mctp 3 32b Opsec 17 Pdf



Fas Org Irp Doddir Dod Jp3 13 3 Pdf



Www Standards Doe Gov Standards Documents 10 1233 Bhdbk 19 Images File




What Is Opsec A Process For Protecting Critical Information Cso Online




Operations Security Opsec Scholar S Choice Edition U S Air Force Amazon Com Books




Pdf Social Media And Opsec An Analysis Through Sociology Of Security



Online Privacy Through Opsec And Compartmentalization Part 3



Info Publicintelligence Net Ioss Terrorismthreathandbook Pdf



2




Ppt Operations Security Opsec Powerpoint Presentation Free Download Id




David Groep Nikhef Pdp Trust Policy Coordination Opsec




What Is The Last Step In The Opsec Process 18 Aboblist




Navy Tactics Techniques And Procedures Nttp 3 54m Mctp 3 32b Formerly Mcwp 3 40 9 Operations Security Opsec March 09 Us Navy United States Government Amazon Com Books



Operations Security Opsec U S Navy



Chips Articles New Navy Opsec App Is Out



Fas Org Irp Doddir Dod D55 02 Pdf




David Groep Nikhef Pdp Trust Policy Coordination Opsec




Opsec For Pc Free Download Windows 7 8 10 Edition




Us Jpm s Opsec 06 Pdf Classified Information Classified Information In The United States



Online Privacy Through Opsec And Compartmentalization Part 3



David Groep Nikhef Pdp Trust Policy Coordination Opsec




Pdf Social Media And Opsec An Analysis Through Sociology Of Security




What Is Operations Security Opsec Upguard




Opsec History And Basics



2




Mco Pli 18 May 07 Pdf Free Download



Www Marines Mil Portals 59 Publications Mco 3070 2a Pdf




What Is Opsec Operations Security



What Is Opsec Operations Security




Operations Security Wikipedia



Www Ceeol Com Content Files Document 7396 Pdf



Usacac Army Mil Sites Default Files Documents Fmpc Atp 3 13 3 Army Operations Security For Division And Below Pdf




Opsec For Pc Free Download Windows 7 8 10 Edition



Media Defense Gov Oct 28 1 1 0 Nttp 3 13 3m Mctp 3 32b Opsec 17 Pdf



2




The Opsec Of Protesting Professionally Evil Insights




Pdf Social Media And Opsec An Analysis Through Sociology Of Security M Kubilay Akman Academia Edu




Operational Security Opsec The Savannah Arsenal Project




Panda Antivirus For Cvp Firewall Opsec



Download Opsec Free For Android Opsec Apk Download Steprimo Com




Pdf Social Media And Opsec An Analysis Through Sociology Of Security



How To Make A Prepper Opsec Plan




What Is The Last Step In The Opsec Process 18 Aboblist




Operations Security Opsec Nttp 3 13 3m Mctp 3 32b Navy Department Of The Amazon Com Books




Opsec For Pc Free Download Windows 7 8 10 Edition



The Art And Practice Of Opsec By T H Survivalblog Com




Operations Security Opsec Af Wingmoms



Media Defense Gov Oct 28 1 1 0 Nttp 3 13 3m Mctp 3 32b Opsec 17 Pdf



Energy Gov Sites Prod Files Oeprod Documentsandmedia Opsec Recommended Practice Pdf




Chesbro On Security Operations Security Opsec



Ppt Opsec Security Awareness Training Powerpoint Presentation Free Download Id




Ppt Topic 6 Security Enabling Objectives Powerpoint Presentation Free Download Id




5 Most Popular Web App Security Testing Methodologies


コメント
コメントを投稿